
Cyberattacks are increasing worldwide. In 2020, cyberattacks, which refer to any malicious maneuver targeting personal computers, computer information systems, or computer networks, were the fifth top-rated risk. By 2021, there were approximately 50% more cyberattacks on corporate networks per week, and by 2025, analysts project cybercrime will cost companies worldwide around $10 trillion, which is up considerably from the $3 trillion in 2015.
Even large-cap companies like Nvidia and Samsung experienced data breaches at the start of this year. These statistics are worrying since the growth of cybercrime over the last few years highlights some significant omissions and vulnerabilities in security by companies across the world.
Cybercriminals Are Everywhere
Yet, cybercriminals are not only targeting corporate networks. Anyone can be a potential victim. In fact, research has found that since there are roughly 2,200 cyberattacks every day, that means over 800,000 people are at risk of being hacked per year. In some instances, these breaches have not been the account holder’s fault since different forms of malware like worms, viruses, and Trojan horses may have deceived them. That said, some successful cyberattacks by hackers have come down to an individual’s poor account security.
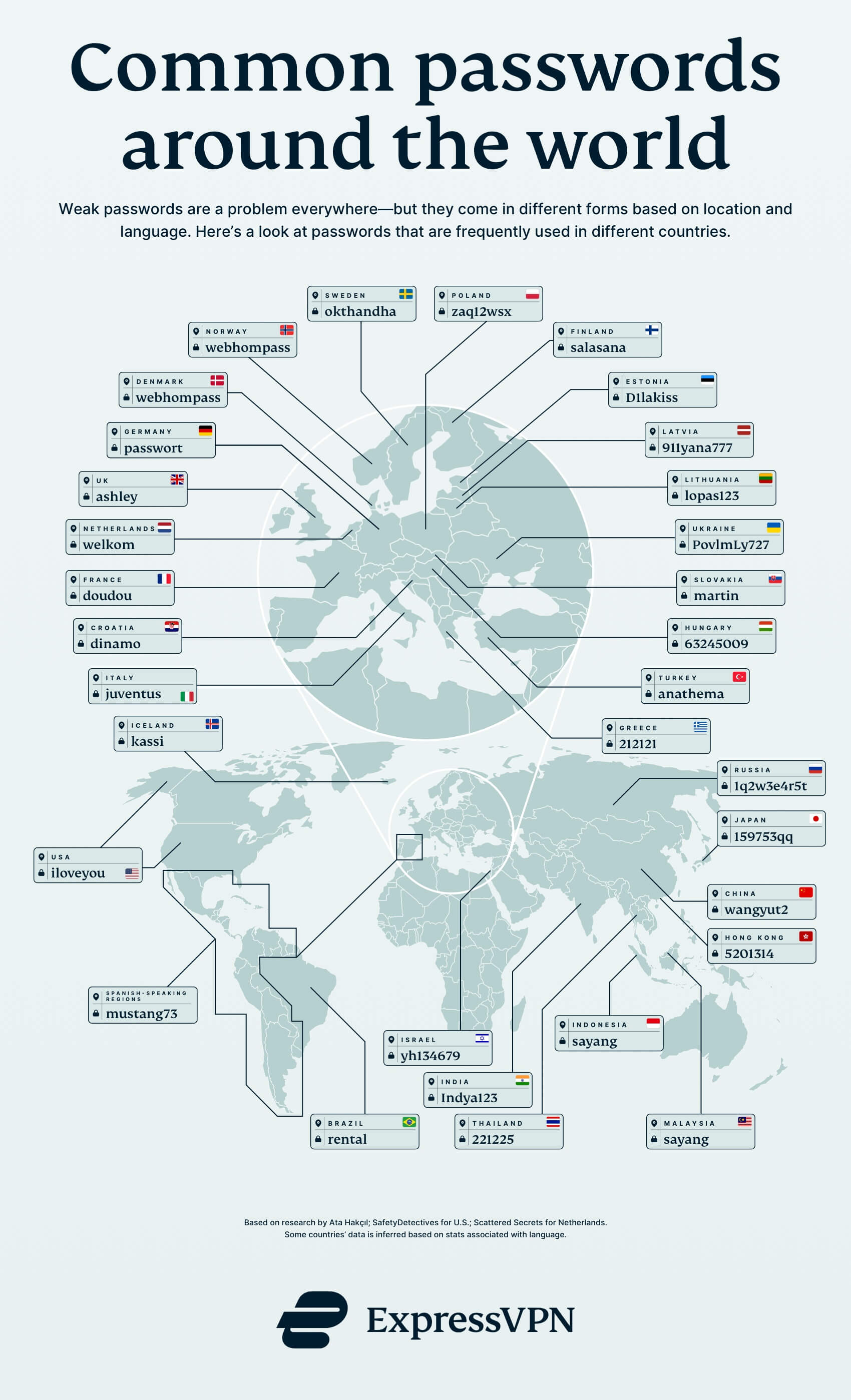
For example, poor password selection is one of the main ways cybercriminals gain access to personal accounts and computers. As this recent infographic on the most common passwords (by country) highlights, the average person uses the same password for several websites.
The study also found that many of these passwords contain common personal details. Some of these details include first name (42.30%), last name (40.00%), social security number (30.30%), and pet animal names (43.80%).
Some survey respondents (26.10%) even indicated they use their ex-partner’s name in their password. Since society has become accustomed to sharing everything about their lives on social media platforms like Instagram and Facebook, personal details like this are very easy for cybercriminals to find.
As mentioned, it is easy to be deceived by malware programs, so individuals can’t be too hard on themselves. However, it’s important to recognize this lack of downloading preventative measures like anti-virus and anti-malware programs has also helped hackers gain access to personal computers.
As technology has become more advanced, so have cybercriminals who now know how to use malware software to intentionally swindle users into thinking they are a trusted third party.
Today, it is increasingly more challenging to know if the Instagram, Facebook, or Twitter ad you are clicking on is legitimate or just another malicious attempt to deceive you and steal your personal information. For these reasons, everyone should look into downloading trusted anti-malware software programs.
Attacking Secure Technologies
Possibly even more worrying is that today’s revolutionary technologies can also be subject to cyberattacks. Blockchain technology, in particular, has transformed business operations across the world by offering decentralization.
This decentralization and ability to work on a peer-to-peer network without the need for a third party have instilled transparency, trust, and security. However, blockchain technology is not immune to cyberattacks, as many people have come to believe.
Recently, we have seen a few situations where hackers have been able to access the blockchain, including during the verification process, the creation of the blockchain, and on exchanges where users are trading cryptocurrencies.
For example, if there are security errors or glitches during the creation of a blockchain, hackers may recognize these vulnerabilities and use them to carry out an attack. Likewise, if an exchange has weak security protocols, cybercriminals have an easier time accessing important account data.
Unfortunately, hackers have capitalized on this realization that blockchain has as many vulnerabilities, in terms of security, as other technologies, stealing roughly $2 billion in blockchain cryptocurrency since 2017.
Much like having a solid password across all of your accounts to avoid cyberattacks, exchange traders also have to be wary of cybercriminals. To avoid becoming a victim, traders should ensure they are not using an exchange that has previously been attacked or had any other issues relating to poor security measures.
The same applies to anyone considering the use of smart contracts, which refer to computer programs on a blockchain that activate when predetermined requirements are met.
When we think about cyberattacks, individual accounts and corporate networks tend to be the most common victims, whereas technologies, such as blockchain, that promote transparency and security are not. However, as we have seen over the last few years, any person, company, or technology is at risk of data breaches.
As a result, it is crucial to implement good cybersecurity practices, including using strong passwords and researching the exchange you are thinking about using. Internet users should also make sure they download all of the available anti-malware programs to avoid Trojan horses and viruses.
Other Useful Blockchain Articles
- Cryptocurrency, Bitcoin, Blockchain Guide
- Blockchain Technology – What It Is?
- Blockchain Explained In Simple Words
- What is Blockchain Ethereum – How Does It Work?
- Blockchain Tutorial For Beginners
- How The Blockchain Transfer System works
- What is a Smart Contract on Blockchain
- Blockchain Forks – What Is A Fork, Soft Fork And Hard Fork
- What Is Blockchain Wallet – Why You Need It
- The Future Of Blockchain Technology – Every Company Will Use Blockchain
- Top 10 Benefits of Blockchain Technology for Business
- Blockchain Companies Improving Food Industry
- Blockchain In Healthcare
